Prominent business and also city governments located primarily in Asia are the subjects of targeted strikes by a previously undocumented espionage group called Worok that has actually been active because late 2020.
“Worok’s tool set consists of a C++ loader CLRLoad, a PowerShell backdoor PowHeartBeat, and a C# loader PNGLoad that makes use of steganography to remove hidden harmful hauls from PNG data,” ESET researcher Thibaut Passilly stated in a brand-new report released today.
Worok is said to share overlaps in tools as well as rate of interests with one more adversarial collective tracked as TA428, with the group linked to strikes against entities extending power, financial, maritime, and telecommunications sectors in Asia in addition to a federal government agency in the center East and also a personal company in southerly Africa.

Malicious tasks embarked on by the group experienced a visible break from May 2021 to January 2022, before returning to the next month. The Slovak cybersecurity firm examined the group’s objectives to be lined up with information theft.
First foothold to target networks with 2021 and also 2022 entailed making use of ProxyShell exploits in choose instances, adhered to by deploying extra customized backdoors for entrenched gain access to. Various other initial concession routes are unidentified yet.
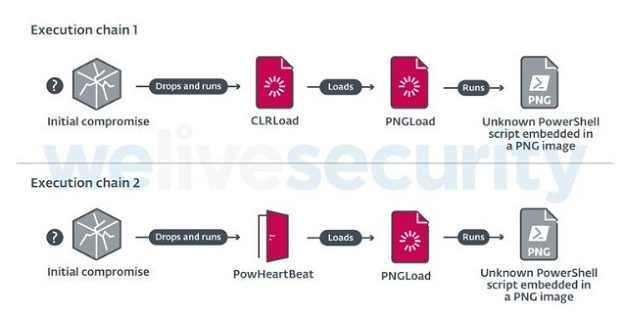
Amongst the tools in Worok’s malware toolbox is a first-stage loader called CLRLoad, which is been successful by a.NET-based steganographic loader codenamed PNGLoad that’s capable of carrying out an unknown PowerShell manuscript embedded in a PNG photo data.
Infection chains in 2022 have actually because gone down CLRLoad in favor of a full-featured PowerShell implant referred to as PowHeartBeat that’s subsequently utilized to release PNGLoad, in addition to connecting with a remote server via HTTP or ICMP to execute approximate commands, send and also receive documents, and perform associated documents procedures.
ESET claimed it was not able to get any of the final-stage PNG payloads, although it’s presumed that the malware could be hidden in legitimate, innocuous-looking PNG images and also for that reason “conceal in plain view” without attracting attention.
“Worok is a cyber espionage team that creates its very own tools, in addition to leveraging existing devices, to jeopardize its targets,” Passilly claimed.
“Stealing details from their targets is what we believe the operators seek due to the fact that they concentrate on prominent entities in Asia and also Africa, targeting numerous fields, both personal and also public, but with a details emphasis on federal government entities.”
In the adhering to sections, we’ll look at 4 standard yet solid reasons Vinchin is the very best Hyper-V backup software application:
1. COMPLETE AND UP-TO-DATE
Vinchin is a thorough back-up service that uses Resilient Adjustment Monitoring (RCT) innovation to supply step-by-step and also differential backups of Hyper-V virtual makers, causing optimal effectiveness and also space cost savings. The back-up is carried out behind-the-scenes to make sure that the computer systems’ features are not disrupted.
2. RECUPERATION ON LOTS LEVELS
Vinchin sustains both granular recuperation of private files as well as automatic recovery of the entire digital equipment across multiple hosts (file-level recuperation). Vinchin additionally uses simply Microsoft typical modern technologies as well as formats (VHD/ VHDX) instead of exclusive ones.
3. IT IS EASY TO USE AND ALSO EXTREMELY RELYABLE
Vinchin back-up remedies incorporate basic cloud backups with the guarantee of a strong and also highly reliable application, as demonstrated by the 10s of hundreds of businesses that use Vinchin back-up solutions throughout the world.
4. EXTRAORDINARY WORTH
Vinchin gives an outstanding price/performance ratio: a solitary perpetual certificate secures an unrestricted number of virtual equipments (available using an organization network) without any restriction or concealed expenses.




